Okta integration using OIDC#
If you are using Okta as an OpenID Connect provider, you can follow these instructions to integrate your instance of Keycloak, enabling your end users to log in to Package Security Manager (On-prem) using Okta.
Prerequisites#
You must have administrator privileges in both Keycloak and Okta to complete this procedure.
Integrating Okta with Keycloak#
Log in to Okta.
Select Applications from the left-hand menu, then click Create App Integration.
Select OIDC - OpenID Connect as your Sign-in method.
Select Web Application as your Application type.
Click Next.
Rename the Web app and keep this browser tab open for now. Open a new tab and log in to Keycloak.
Verify you are in the dev realm.
Select Identity providers from the left-hand menu.
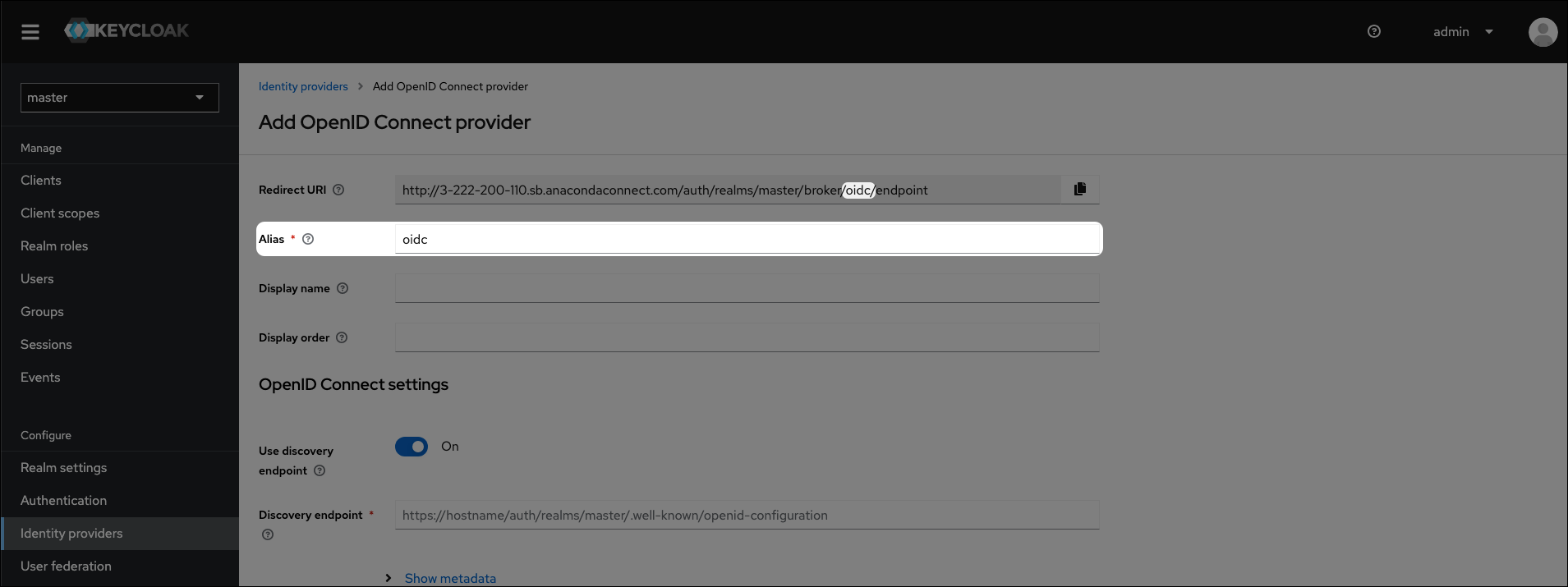
Click OpenID Connect v1.0.
Set the Alias and Display name for your provider.
Copy the Redirect URI from Keycloak.
Return to your Okta tab and add the URI you just copied from Keycloak to Sign-in redirect URIs.
Optionally, add a URL to the Sign-out redirect URIs. Anaconda recommends returning your end users back to your organization’s Okta dashboard for a more complete user experience.
Click Save.
Note
Now that you’ve created your App Integration, you have a Client ID and a Client Secret for your application.
Copy the Client ID and Client Secret and paste their values into their respective fields in Keycloak, under OpenID Connect Settings.
If necessary, toggle Use discovery endpoint to
OFF.Enter the Authorization URL and Token URL in their respective fields.
Note
You can view the URLs you need by opening a browser and navigating to the following URL:
# Replace <OKTA_URL> with your organizations Okta URL # Replace <CLIENT_ID> with the Client ID of the application you just created https://<OKTA_URL>/oauth2/default/.well-known/openid-configuration?client_id=<CLIENT_ID>``
Click Add.
Return to Okta and assign the application to users or groups that require access to Package Security Manager.
Test your setup by logging in to Package Security Manager using an Okta user account.